If you have multiple GitHub accounts, you may want to use them on the same machine without entering your username and password every time you push or pull. In this article, I will show you how to use SSH keys to manage multiple GitHub accounts on a single machine.
This article will guide you through the process of setting up multiple GitHub accounts with SSH, allowing you to access them easily without ever needing to enter your password again. Get ready to juggle your accounts like a pro!
Why Use Multiple Git Accounts?
Many developers contribute to both personal and professional projects. Using separate Git accounts helps:
- Keep work and personal commits separate
- Maintain privacy and security
- Comply with company policies
- Avoid accidental pushes to the wrong repository
Overview of SSH and Git Authentication
SSH (Secure Shell) is a protocol for secure remote login and other secure network services. Git can use SSH keys for authentication, allowing you to securely connect to services like GitHub, GitLab, and Bitbucket without entering your password every time.
Step 1: Generate SSH Keys
The first step is to generate an SSH key for each of your GitHub accounts. Each account will have its own private key (kept safe on your machine) and public key (shared with GitHub for authentication).
Open your terminal and run the following commands for each account (replace email and key name as needed):
# Default account (will be saved to the default file ~/.ssh/id_ed25519)
ssh-keygen -t ed25519 -C "your_personal_email@example.com"
# Company account
ssh-keygen -t ed25519 -C "your_personal_email@example.com" -f ~/.ssh/work_key -P ""
# Personal account
ssh-keygen -t ed25519 -C "your_company_email@company.com" -f ~/.ssh/personal_key -P ""
# If you are using an older system that does not support Ed25519, use:
ssh-keygen -t rsa -b 4096 -C "your_email@example.com" -f ~/.ssh/your_email -P ""
Repeat this command for each account, naming the key appropriately for each account.
Step 2: Add SSH Keys to SSH Agent
Start the SSH agent and add your keys:
eval "$(ssh-agent -s)"
# For company GitHub account
ssh-add ~/.ssh/work_key
# For personal GitHub account
ssh-add ~/.ssh/personal_key
Step 3: Add SSH Keys to GitHub
- Copy the contents of each public key:
cat ~/.ssh/work_key.pub # Copy key for company account
cat ~/.ssh/personal_key.pub # Copy key for personal account
- In the upper-right corner of any GitHub page, click your profile photo, then click Settings. You can access settings at: https://github.com/settings/profile
- In the "Access" section of the sidebar, click "SSH and GPG keys".
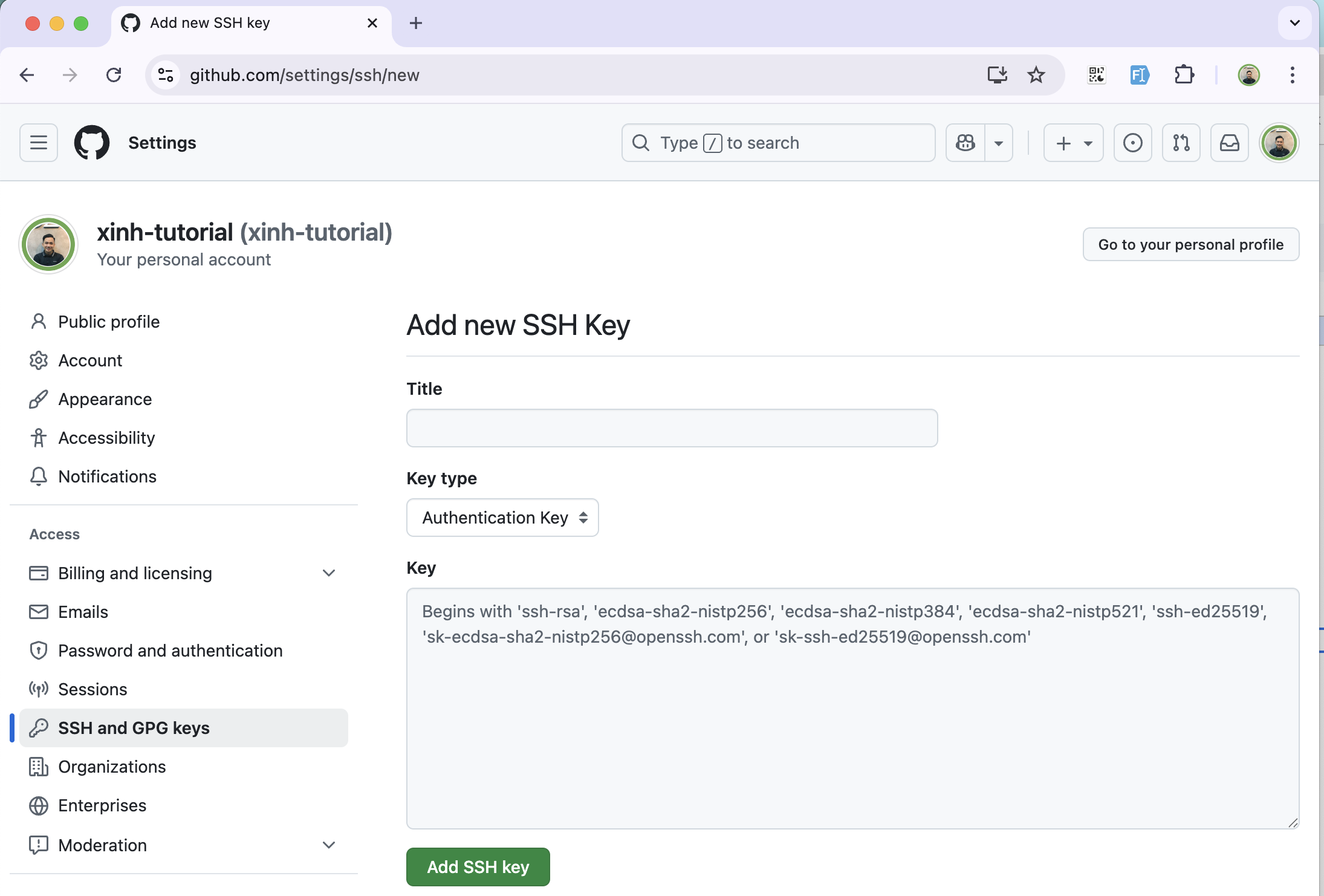
- Click "New SSH key" or "Add SSH key". Direct link: https://github.com/settings/ssh/new
- In the "Title" field, add a descriptive label for the new key. For example, if you use a personal laptop, you might name it "Personal laptop".
- Choose the key type. Leave as default: "Authentication key".
- In the "Key" field, paste your public key.
- Click "Add SSH key".
- If prompted, confirm access to your GitHub account.
Step 4: Create SSH Config File
Create or edit the ~/.ssh/config file:
vi ~/.ssh/config
Host github-work
HostName github.com
IdentityFile ~/.ssh/work_key
IdentitiesOnly yes
Host github-personal
HostName github.com
IdentityFile ~/.ssh/personal_key
IdentitiesOnly yes
Replace work_key and personal_key with your actual key paths. Each Host block defines a unique alias (e.g., "github-work") for easy access.
Step 5: Clone Repositories
When cloning repositories, use the appropriate host alias for each account:
# Clone personal repo
git clone git@github-personal:username/repo.git
# Clone company repo
git clone git@github-company:company/repo.git
No authentication required. You can easily switch between your GitHub identities.
Now you have successfully set up multiple GitHub accounts with multiple SSH keys on your machine. You can easily switch between accounts and contribute to different projects without any conflicts.
Set user for each repository
cd path/to/repo
git config user.name "Your Name"
git config user.email "your_email@example.com"
Comparison Table: Using SSH vs HTTPS for Multiple Git Accounts
| Criteria | SSH (Recommended) | HTTPS |
|---|---|---|
| Security | High (private key) | Medium (password) |
| Multiple accounts | Easy with SSH config | Hard, need to re-login |
| Automation | Easy (no password) | Often need password |
| CI/CD support | Good | May be limited |
| Key management | Flexible | Not supported |
Common Issues and Solutions
Error: Permission denied (publickey)
- Check if you have added the correct SSH key to GitHub/GitLab
- Check if your
~/.ssh/configfile is correct - Use
ssh -T git@github-personalto test the connection
Error: Committed with wrong account
- Check your user/email config in the repo with
git config --list - Use
git config user.nameandgit config user.emailto update
Notes
Keep your private keys safe. Consider using a passphrase for extra security. Never share your private key with anyone!
Best Practices
- Use descriptive key names (e.g.,
id_ed25519_work) - Never share your private keys
- Regularly rotate your SSH keys
- Use passphrases for added security
- Backup your SSH config and keys securely
FAQ
Q: Can I use this method for GitLab, Bitbucket, etc.? A: Yes, just add corresponding Host blocks in your SSH config.
Q: Can I use the same key for multiple accounts? A: It's not recommended for security and audit reasons.
Q: How do I check which key is being used?
A: Use ssh -T git@github-personal or ssh -T git@github-work to test the connection.
Conclusion
Configuring multiple Git accounts with SSH helps developers work more securely and professionally across multiple projects. Apply the above steps to optimize your personal and business workflow.
